SAP GRC and Cybersecurity
Reimagine risk and compliance with integrated, automated, and embedded solutions to protect your business
Gain early and predictive insight into anomalies and potential risks
Continuously monitor risks, identities, cyberthreats, and compliance across your mission-critical systems and processes with SAP GRC and cybersecurity solutions.
Leverage predictive capabilities for improved risk management
Adopt the Three Lines Model recommended by the Institute of Internal Auditors and others by linking operations, risk management, compliance, and internal audit. SAP GRC solutions support automation for tasks and decision-making, real-time visibility with continuous control monitoring, and predictive analytics to inform business operations and planning.
Optimize global trade with agile compliance processes
Conduct trade in evolving global markets with greater confidence and agility. With SAP solutions, you can maximize the potential of trade strategies and partnerships by centrally managing trade compliance based on ever-evolving regulatory requirements, geopolitical risks, changing market opportunities, tariffs, trade agreements, and other customs processes.
Reduce cyberthreats and manage user identities
Protect your company’s reputation and intellectual property enterprise-wide. Flexible solutions for cyberthreat monitoring, data controlling, identity and access governance, and privacy management help keep systems and data more secure in a continuously changing environment while enabling powerful and flexible monitoring, detection, and response.
GRC and cybersecurity solutions

Manage financial, vendor, and operational risk
Get detailed insight into how risk drivers can impact your business value and reputation for smart, risk-aware decisions with our enterprise risk management (ERM) software.
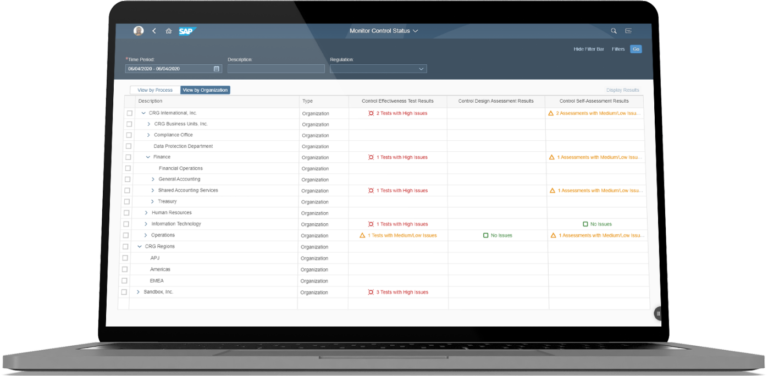
Control key processes and manage compliance
Document, assess, test, and remediate critical process risks and controls by streamlining enterprise compliance efforts and using best practice internal control processes.

Monitor the adequacy of financial controls
Automate internal controls for financial reporting that contain content from SAP S/4HANA, whether it’s on premise or in the cloud.
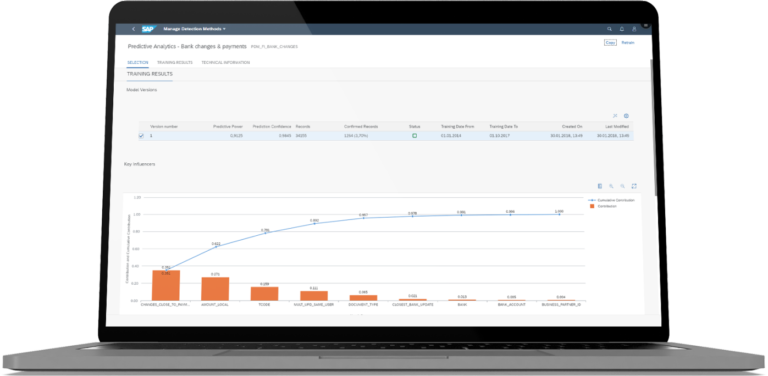
Detect fraud and investigate suspicious patterns faster
Screen large volumes of transactional data in real time based on predictive analyses and extensible rule sets that uncover anomalies, fraud, or deviations from policy.
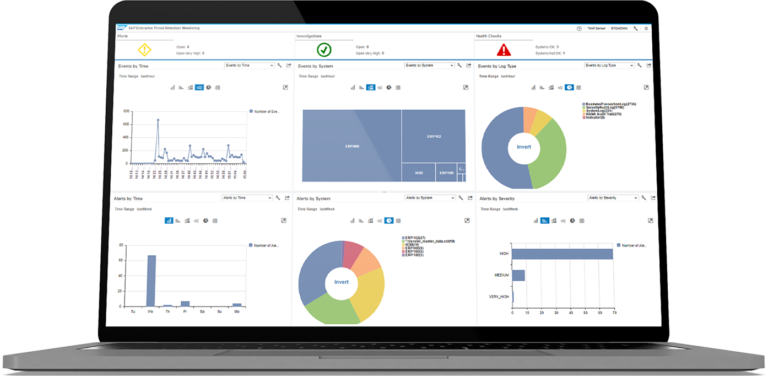
Address cyberthreats with real-time intelligence
Help identify, analyze, and address cyberattacks while they’re happening in your SAP applications with our security information and event management (SIEM) tool.
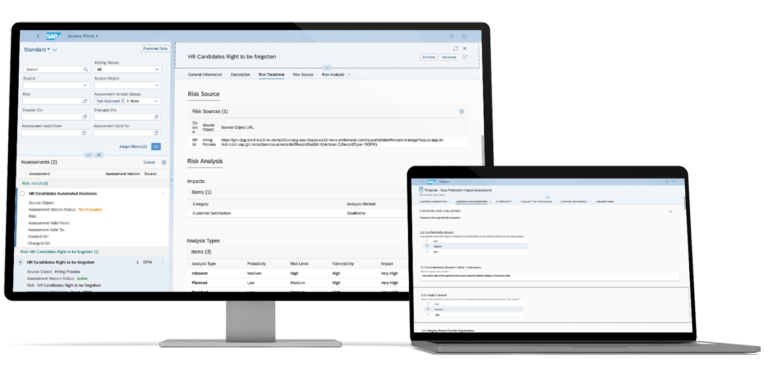
Manage and comply with evolving data privacy regulations
Simplify privacy and security requirements, operationalize privacy management activities, and manage the data subject rights request lifecycle.
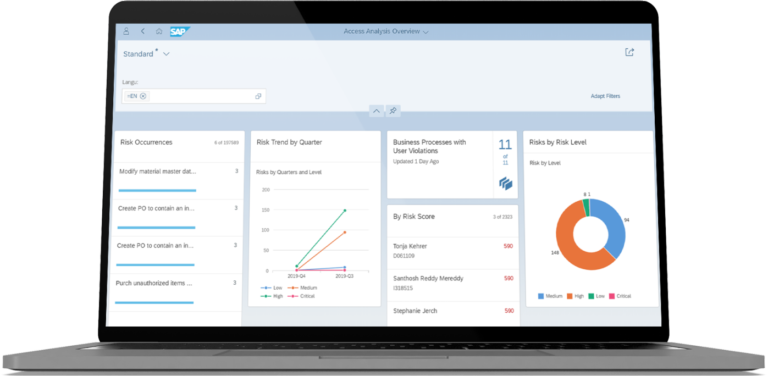
Detect and remediate access risk violations
Automate user provisioning, role management, privileged access, and periodic certification while continuously monitoring users and applications for risk.
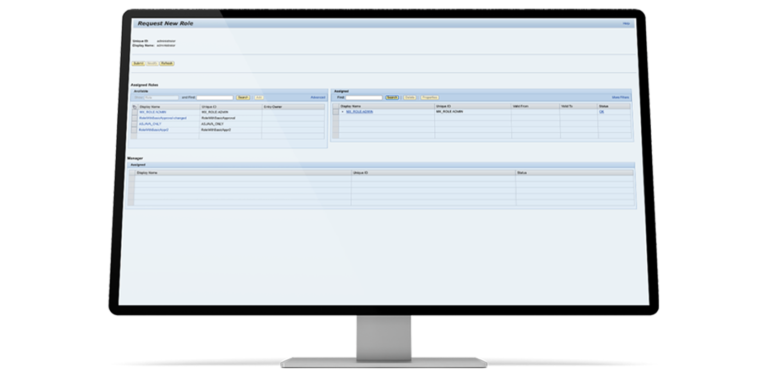
Simplify access management in complex environments
Deliver an intuitive sign-on experience and use dashboards to pinpoint issues, adjust user access dynamically, improve access compliance, and resolve risks quickly.
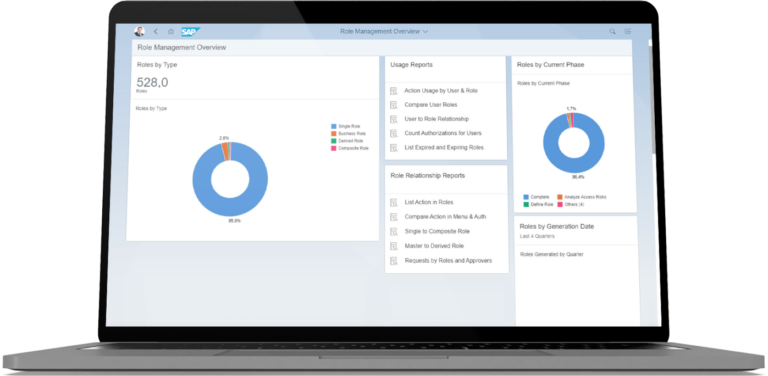
Manage user access in heterogeneous environments
Embed identity management into your business processes and centralize user access management across your enterprise.
Enable simple and secure access to business applications
Enhance the user experience, strengthen security, and streamline administration with simple and secure user authentication.
Question? Get In Touch!
Let’s talk, simply contact us and an expert will get in touch with you as soon as possible
Don't hesitate to contact us
(+84) 888 780 670